Key management reporting has become a critical part of cybersecurity compliance in 2025. Companies are now required to track and document every aspect of cryptographic key usage to meet stricter regulations, improve operational security, and build trust. Here’s what you need to know:
- Stricter Regulations: The SEC now requires faster incident reporting for cyber events, with deadlines as short as four business days. Global standards like ISO 27001 and NIST are also shaping compliance practices.
- AI and Automation: Real-time monitoring and AI tools are replacing manual processes, cutting compliance delays by 50% and reducing errors.
- Web3 Challenges: Decentralized models, such as blockchain and multi-signature wallets, complicate compliance. Companies must implement systems that track key usage while meeting audit requirements.
- Zero Trust and Privacy: Organizations are integrating Zero Trust principles and privacy-by-design into key management, ensuring every access request is verified and logged.
Preparing for these changes involves centralizing key inventories, automating reporting, and aligning with global standards. For businesses in digital finance and Web3, robust cryptographic controls are now essential to meet regulatory expectations and maintain market access.
How Does Key Management Improve SaaS Compliance?
New Regulatory Requirements for Key Management Reporting
By 2025, regulatory authorities will elevate key management reporting to a central pillar of cybersecurity compliance. No longer seen as just an IT issue, key management is increasingly viewed as a critical component of an organization’s overall security strategy. This shift is encouraging companies to weave detailed reporting into their broader risk management and governance processes, aligning with the anticipated updates to SEC guidelines.
SEC Cyber Disclosure Rules and Reporting Requirements
Upcoming changes to U.S. cyber disclosure rules are set to include key management incidents under their umbrella. While the specifics are still pending, businesses should prepare for stricter and time-sensitive incident reporting requirements. To meet these demands, companies will need to fine-tune their incident investigation processes and maintain thorough audit trails to ensure compliance.
Global Standards for Key Management Compliance
Regulatory changes aren’t limited to the U.S.; global standards are also reshaping key management practices. Frameworks like NIST SP 800-57 and ISO/IEC 27001 outline best practices for managing the entire key lifecycle, from creation to destruction. Meanwhile, evolving regulations such as the AMLA Travel Rule and the EU’s Digital Operational Resilience Act (DORA) are expected to stress traceability and the adoption of privacy-by-design principles. For Web3-focused organizations like Bestla VC, aligning with these unified control frameworks can simplify compliance across multiple jurisdictions while ensuring documentation is ready for audits.
To keep up, organizations are turning to advanced compliance tools like centralized platforms and AI-driven anomaly detection. Enhanced training programs, proactive risk assessments, and simulated incident responses are also becoming essential. These measures, combined with the growing adoption of automation and regulatory technology (RegTech) solutions, aim to help companies manage increasing disclosure requirements while maintaining effective risk management practices.
AI and Automation in Key Management Reporting
AI and automation are reshaping how organizations handle key management compliance. Instead of depending on periodic manual reviews and spreadsheet-based workflows, many companies are adopting continuous, real-time monitoring systems. These systems are designed to quickly detect control failures and unauthorized key usage, which is crucial as regulatory scrutiny around cybersecurity and operational resilience intensifies. Automated, verifiable reporting for key lifecycle events – such as generation, rotation, revocation, and access – has become a top priority for boards and executives alike[2,10,12]. This shift relies on two main approaches: automated audits for instant detection and predictive analytics to anticipate risks.
Automated regulatory tracking has significantly reduced compliance delays, cutting them by about 50%[4]. With over 80% of organizations planning to boost their investment in compliance technology by 2025, the transition from manual processes to automated workflows is saving labor hours and reducing human error[9,11]. For companies operating in digital finance or decentralized infrastructures – especially those engaging with specialized investors like Bestla VC – integrating AI-powered systems that handle on-chain key usage and advanced cryptographic schemes is essential. These systems must meet the expectations of both traditional regulators and industry-specific requirements[6].
Automated Audits and Anomaly Detection
As regulatory expectations grow, automated auditing methods are ensuring continuous compliance. These AI-driven systems follow a structured process: they gather data from hardware security modules (HSMs), cloud key management services (like AWS KMS or Azure Key Vault), identity providers, and logging tools; convert compliance policies into machine-readable rules; test controls in real time; and automatically produce compliance reports[2,11].
Using supervised machine learning, these systems classify normal and suspicious key activities, while unsupervised methods like clustering and isolation forests identify anomalies within large volumes of access logs[2,11]. Natural language processing (NLP) also plays a role, analyzing regulatory texts to map required controls to technical configurations. This enables "compliance as code", where key management policies are continuously tested against standards[6]. Such systems can flag issues like unauthorized after-hours access to critical signing keys, sudden increases in decryption operations, or access attempts from unknown IPs[1].
To minimize false positives, these models incorporate business context – such as deployment schedules, quarter-end activities, asset importance, and identity verification measures like multi-factor authentication and device posture[6]. Feedback from compliance and security teams, who classify alerts as valid or benign, helps refine the models for better accuracy over time[1]. Beyond real-time detection, predictive models are now being used to anticipate where control gaps might appear.
Predictive Risk Assessments in Compliance Reporting
Predictive analytics models are transforming compliance reporting by analyzing past incidents, audit findings, and configuration changes to predict where future failures might occur[2,11]. These models assign risk scores based on factors like the number of unmanaged keys, reliance on manual provisioning, policy exceptions, and the frequency of past incidents[1].
With these insights, compliance leaders can prioritize actions such as automating key rotations, centralizing key ownership, or tightening access controls – often ahead of regulatory deadlines or external audits[9,11]. Predictive analytics not only enhances efficiency but also helps organizations avoid compliance failures altogether. For example, 64% of companies aim to use automation for better risk visibility, while 53% are focused on faster issue resolution. Integrating predictive risk scores into governance, risk, and compliance (GRC) tools enables organizations to create reports that not only reflect current compliance status but also highlight future risks tied to key management practices[2,7].
The benefits are clear. Real-time compliance monitoring shortens the time between a control failure and its detection, improving incident response and reducing the risk of regulatory penalties[1]. AI systems also improve accuracy by correlating data from multiple sources and maintaining complete audit trails, which meet examiners’ requirements for traceable cyber and operational risk reports[2,10]. These advancements lower reporting costs, free up staff for more strategic tasks, and strengthen defenses during regulatory evaluations[9,12].
sbb-itb-c5fef17
Data Privacy and Cybersecurity Integration
By 2025, regulators and auditors are pressing organizations to combine cryptographic key management, data protection, and cybersecurity controls into a unified framework. This means businesses must ensure that key generation, storage, rotation, and retirement processes align with data privacy standards and cybersecurity frameworks like NIST and ISO 27001[1][2]. U.S. institutions, in particular, are taking steps to create integrated dashboards that consolidate key lifecycle events, access logs, and incident alerts to meet regulatory compliance requirements[1][2]. This consolidation not only simplifies oversight but also lays the groundwork for adopting advanced key management practices.
To stay ahead, organizations are mapping key management controls to KYC (Know Your Customer) and AML (Anti-Money Laundering) workflows, as well as incident reporting systems. This ensures that any key compromise is quickly identified, reported, and addressed[2][3]. By embedding security into daily operations, businesses make auditing across different standards and jurisdictions more efficient[1]. The shift is also reflected in governance trends: the percentage of S&P 500 companies without a dedicated cybersecurity committee dropped from 15% in 2021 to just 5% by 2024, largely due to SEC rules requiring 95% of boards to oversee cybersecurity directly[2].
Privacy-by-Design in Key Management Systems
Incorporating privacy-by-design principles into key management systems has become a priority, especially for institutions handling KYC and AML processes. Financial organizations are limiting personal data collection to what’s absolutely necessary and ensuring that every key operation is both auditable and tied to a legitimate purpose[2][3].
By 2025, many financial institutions have adopted eKYC solutions that tokenize or pseudonymize identity data. The sensitive mapping between tokens and raw identity attributes is safeguarded under keys stored in hardware security modules (HSMs), minimizing exposure of raw IDs in operational systems[3]. At the point of data capture, personal information is tokenized, and identifiers are encrypted using HSM-protected keys. Downstream systems then rely on tokens for functions like risk scoring, sanctions checks, and transaction monitoring[2][3]. Consent management is tightly integrated with access controls, ensuring that only data covered by active consent and regulatory requirements can be decrypted and accessed[3].
Auditors now routinely request documentation of these systems, including data flow diagrams, key hierarchy diagrams, and Data Protection Impact Assessments (DPIAs)[1][2]. For U.S. organizations, aligning these practices with BSA/AML requirements and state privacy laws like California’s CCPA/CPRA has become standard procedure[1][2][3]. These efforts support the creation of audit-ready, compliant reporting systems.
Zero Trust Security and Cyber Incident Reporting
Building on privacy-by-design, Zero Trust principles offer an additional layer of security by requiring continuous validation for every access request. Unlike traditional models that rely on implicit trust, Zero Trust assumes no user, device, or network location is inherently secure. Every request is verified, authorized, and logged[2].
In key management, this approach means access to cryptographic keys and decrypted data is controlled through robust identity and access management (IAM), multi-factor authentication, device posture checks, and network micro-segmentation[2]. Organizations are adopting identity-centric policies, tying each key operation – like decrypting KYC records – to a specific user, role, device, and context, with real-time evaluations for every action[2]. This aligns with 2025 compliance mandates requiring firms to document "who accessed what, when, why, and how", particularly for sensitive data such as financial records and government IDs[2].
Incident playbooks are now being designed to address cryptographic events, such as suspected key compromises, unauthorized key usage, or HSM failures. These events trigger materiality assessments and may require regulatory notifications[2][8]. Logs from key management systems are increasingly integrated into Security Operations Center (SOC) tools, enabling rapid investigation of unusual key usage patterns. If necessary, incidents can be classified and disclosed within mandated timelines[2]. By adding this identity-focused layer of oversight, organizations strengthen their cybersecurity posture.
For sectors like digital finance and decentralized infrastructures, where cryptographic key control is critical, these Zero Trust measures are non-negotiable. Companies dealing with digital assets or web3 technologies face intense scrutiny, as cryptographic keys often grant direct control over on-chain assets and secure customer data[2][8]. Firms working with specialized investors, such as Bestla VC, which focuses on advanced cryptography and decentralized systems, must demonstrate robust key control and contingency planning to meet regulatory expectations[8].
Preparing for the Future of Key Management Reporting
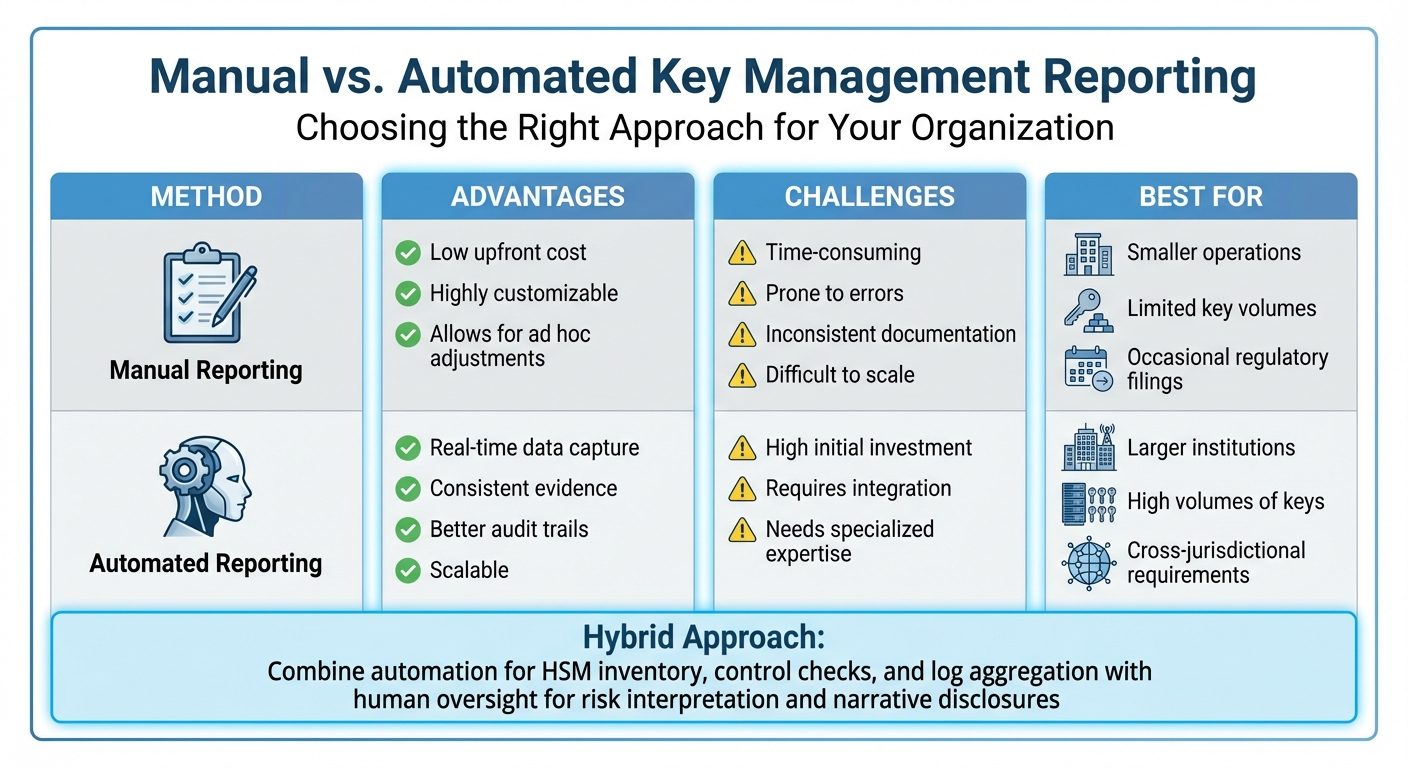
Manual vs Automated Key Management Reporting: Advantages, Challenges, and Use Cases
For U.S. institutions, preparing for future key management reporting starts with a thorough evaluation of their current processes. Begin by creating an inventory of all cryptographic keys, mapping out existing reporting workflows, and identifying relevant regulatory mandates such as those from the SEC, FFIEC, and state privacy laws. This inventory process not only exposes inefficiencies but also highlights opportunities for automation. Organizations should focus on initiatives that reduce the risk of regulatory breaches – like missing incident-reporting deadlines – address existing audit findings, and improve overall efficiency gains[1][4]. This foundational assessment sets the stage for a strategic roadmap aimed at achieving regulatory precision and operational improvements.
Develop a two- to three-year roadmap. Start by consolidating key inventories into a centralized system of record. From there, implement standardized reporting templates aligned with ISO 27001, NIST SP 800-57/53, and SEC requirements. Introduce basic automation features such as alerts, dashboards, and audit logs, and later incorporate advanced AI-driven analytics[1][4]. Budget allocation should balance investment in core platforms, like RegTech or GRC suites, with ongoing monitoring and staff training[4][6].
Choosing between manual and automated approaches depends on factors like organizational scale, regulatory demands, and risk tolerance. Smaller organizations with fewer cryptographic keys and infrequent regulatory filings can enhance manual processes by using standardized checklists, dual reviews, and periodic internal audits[1][4]. However, for mid-to-large financial institutions, fintech companies, and web3 firms, the complexity of operations makes manual-only approaches impractical. If delays or errors in manual processes jeopardize compliance timelines or incident reporting, it’s time to shift toward automated evidence collection and real-time monitoring[4][5][6].
Manual vs. Automated Reporting Approaches
| Method | Advantages | Challenges | Key Management Relevance |
|---|---|---|---|
| Manual Reporting | Low upfront cost; highly customizable; allows for ad hoc adjustments | Time-consuming; prone to errors; inconsistent documentation; difficult to scale | Suitable for smaller operations with limited key volumes and occasional regulatory filings[1][4] |
| Automated Reporting | Real-time data capture; consistent evidence; better audit trails; scalable | High initial investment; requires integration and specialized expertise | Ideal for larger institutions managing high volumes of keys and cross-jurisdictional regulatory requirements[1][4][5][6] |
A hybrid approach provides a balance between cost and functionality. Automation can handle tasks like HSM inventory, control checks, log aggregation, and compliance dashboards, while human oversight remains essential for interpreting risks, addressing exceptions, and crafting narrative disclosures. For instance, automation can continuously collect and normalize logs related to key usage and access, while compliance analysts manually review anomalies and prepare SEC-compliant incident reports as needed. This combination ensures robust controls while maintaining informed oversight, meeting regulatory expectations on both fronts[1][4][6].
Web3 and digital asset institutions face increased scrutiny around private key governance, multi-sig controls, and custody arrangements. These organizations must thoroughly document processes for key generation, storage, rotation, and recovery, as well as ensure proper segregation of duties and access approvals[6][7]. Firms supported by Bestla VC, for example, can use advanced cryptographic tools and decentralized infrastructures to integrate on-chain controls with traditional compliance reporting. This integration helps bridge the gap between blockchain-based management and off-chain regulatory requirements, satisfying both digital-asset regulators and traditional institutional stakeholders[6][7].
Conclusion
Key management reporting compliance in 2025 is shaped by tighter regulations, increased use of AI automation, and deeper integration of cybersecurity measures. Rapid incident response has become a regulatory necessity. For instance, the critical infrastructure requirements under CIRCIA, effective October 2025, mandate real-time responsiveness that manual processes simply can’t keep up with[2]. At the same time, board-level oversight of cybersecurity has gained significant attention, emphasizing that governance accountability is no longer optional[2].
In line with these regulatory shifts, advanced compliance platforms are now enabling a more proactive approach to risk management. Automation plays a critical role in handling complex key inventories, with many businesses turning to cloud-based solutions for continuous oversight. Enterprises leveraging AI-powered RegTech platforms have reduced compliance delays by 50% by automating regulatory tracking and anomaly detection[4][1]. This shift reframes compliance from a reactive obligation into a strategic advantage.
Cybersecurity integration remains a cornerstone of these efforts. Zero Trust architectures and privacy-by-design principles are becoming standard tools for addressing the growing threat landscape. With the compliance data management market projected to hit $16.6 billion, organizations must incorporate real-time monitoring and identity access management into their key management strategies[4][3]. These enhancements not only strengthen security but also create audit trails that satisfy both regulators and internal stakeholders.
Sustaining these advancements requires strategic investments and a shift in corporate culture. With 82% of companies increasing their budgets for compliance technology, businesses should focus on unified control frameworks, seamless integration of enterprise systems, and active board-level involvement in compliance planning[4][1]. For digital asset and web3 firms, aligning decentralized technologies with established reporting standards will be critical to navigating complex regulatory landscapes. Meanwhile, firms like Bestla VC are pushing forward with innovative investment strategies to support this evolution.
FAQs
How are AI and automation transforming compliance in key management reporting?
AI and automation are transforming how compliance is handled in key management reporting by making processes more precise and minimizing the chances of human error. By automating data collection and reporting, these technologies help businesses keep pace with constantly evolving regulations.
On top of that, real-time monitoring and auditing tools enable companies to spot and resolve compliance issues before they escalate. This approach not only streamlines operations but also lowers the risk of expensive fines or interruptions.
What compliance challenges arise with decentralized technologies like blockchain?
Decentralized technologies, like blockchain, come with their own set of compliance hurdles. One major issue is the difficulty in applying traditional regulations. Without a central authority to oversee operations, maintaining control and enforcing rules becomes far more complicated. On top of that, the pseudonymous nature of blockchain users can make it harder to achieve the transparency and accountability that many regulations demand.
Another challenge stems from distributed governance. Since decision-making is often shared among multiple stakeholders, meeting standardized reporting requirements can become a logistical headache. To navigate these complexities, organizations need to rethink their approach – crafting new strategies and using advanced tools to stay compliant in these decentralized systems.
Why is adopting Zero Trust principles important for effective key management?
Adopting Zero Trust principles is a smart move for managing cryptographic keys effectively. It minimizes the chances of unauthorized access, ensures continuous verification of users and devices, and strengthens the overall security of sensitive keys. With stricter compliance standards looming in 2025, this strategy helps organizations stay prepared for emerging security challenges.
By focusing on Zero Trust, companies can better protect their critical assets, meet regulatory requirements, and create a stronger, more adaptable security framework in today’s ever-evolving digital world.